which of the following categories require a privileged access agreement
Apply real-time vulnerability and threat data about a user or an asset to enable dynamic risk-based access decisions. The types of privileged accounts typically found in an enterprise environment include.
Understanding Privileged Access Management Pam Strongdm
Which of the following categories require a privileged access agreement.

. Local Administrative Accounts are non-personal accounts that provide administrative access to the. Both IA Technical IA Management b. In the provisions of the Information Security and.
Cyber Security Fundamentals 2020 Pre-Test This exam works as a test out. Privileged access may be used only. 21 Maintain an up-to-date inventory of all privileged accounts.
Create an access policy. A user access agreement is usually one part of an employee code of conduct. Privileged Access Management PAM refers to a class of solutions that help secure control manage and monitor privileged access to critical assets.
Privileged access shall be granted to individuals only after they have read and signed this Agreement. Keep an inventory of privileged accounts for critical Active Directory groups such as Domain Admins admin and root accounts for unix. Nel who require privileged accesselevated privileges to Army Information Systems.
Therefore the idea of specific categories doesnt really. Both IA Management CNDSP c. Create an approvers group.
There can be a privileged-level access agreement for almost any sort of computer system contract document or software application. Which agreement would need to be read carefully and signed by a network administrator not an end user in the Sales department. Restricting privi leged accounts to specific personnel.
Privileged-level access is granted to authorized personnels that could affect the important files data network communications etc. The privileged user agreement targets administrators and others who. Organizations need to employ an ongoing program to pair with an advanced deployed strategy.
For instance this capability can allow. To know who has. Privileged access is granted only to authorized individuals.
Which of the following categories require a privileged access agreement. Which of the following certifications would satisfy IAM level II and IAM level III. In accordance with AR.
If you own a training company youre probably always looking for new ways to increase the number of. In this article. Which of the following categories require a privileged-level access agreement.
Which of the following categories requires a privileged access agreement. Types of commercial off -the-shelf operating systems. Which of the following Categories Require a Privileged-Level Access Agreement.
Enforce vulnerability-based least-privilege access. Identity and Access Management IAM or Identity Management IdM refers to the general cybersecurity solutions that allow customers to access their accounts or employees to access. Indications of an incident fall into two categories a.
Enable and configure privileged access management. Individuals with privileged access must respect the rights of system users respect the integrity of systems and associated physical resources and comply with all relevant laws or regulations. This answer was confirmed as correct and useful.
IA Technical requires a privileged level access agreement. The following briefly details the Privileged Access Management Lifecycle model which. Individuals are also required to keep.
Define baselines for privileged user activity and privileged access and monitor and alert any deviations that meet a defined risk threshold. D A user access agreement specifies what penalties will be imposed when an employee violates the employee code of. This answer was confirmed as correct and useful.
IA Technical requires a privileged access agreement. Implement threatprivileged user analysis.
Archive Of What S New In Microsoft Defender For Cloud Microsoft Docs

Understanding Privileged Access Management Pam Strongdm
Knowledge Base Article Service Portal
What Are The Different Types Of Penetration Testing Purplesec

Automatically Apply A Retention Label Microsoft Purview Compliance Microsoft Docs

Understanding Privileged Access Management Pam Strongdm

What Is Privileged Access Management Pam Explained Security Wiki

Controlling Access One Element Of Cybersecurity Article The United States Army

Powerful Privileged Access Management Cloud Or On Premises
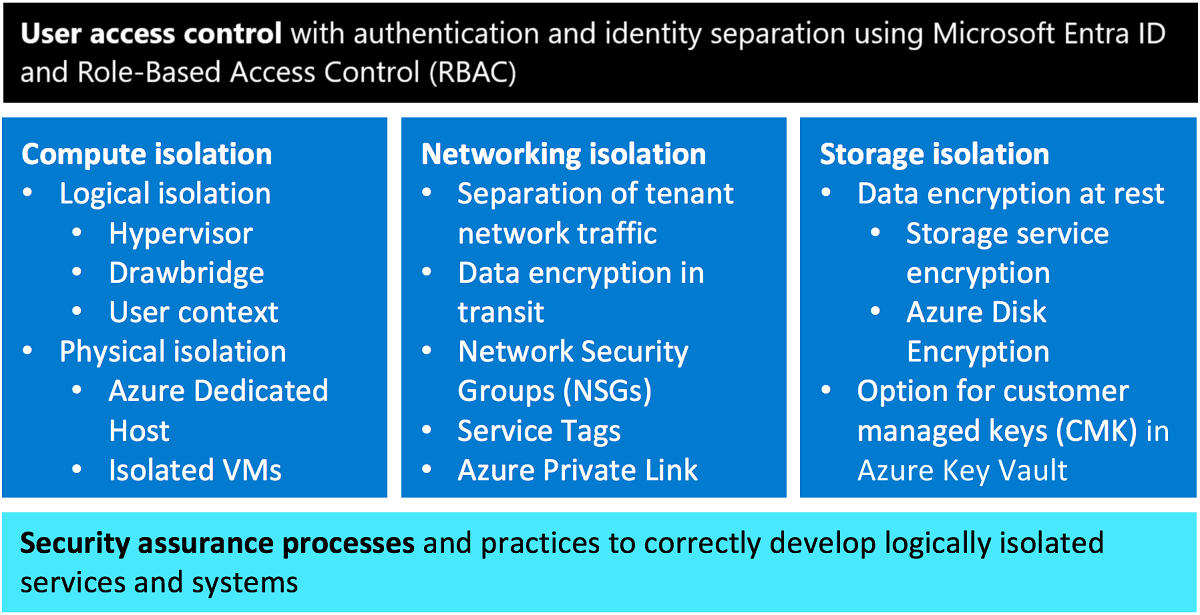
Azure Guidance For Secure Isolation Azure Government Microsoft Docs

Understanding Privileged Access Management Pam Strongdm
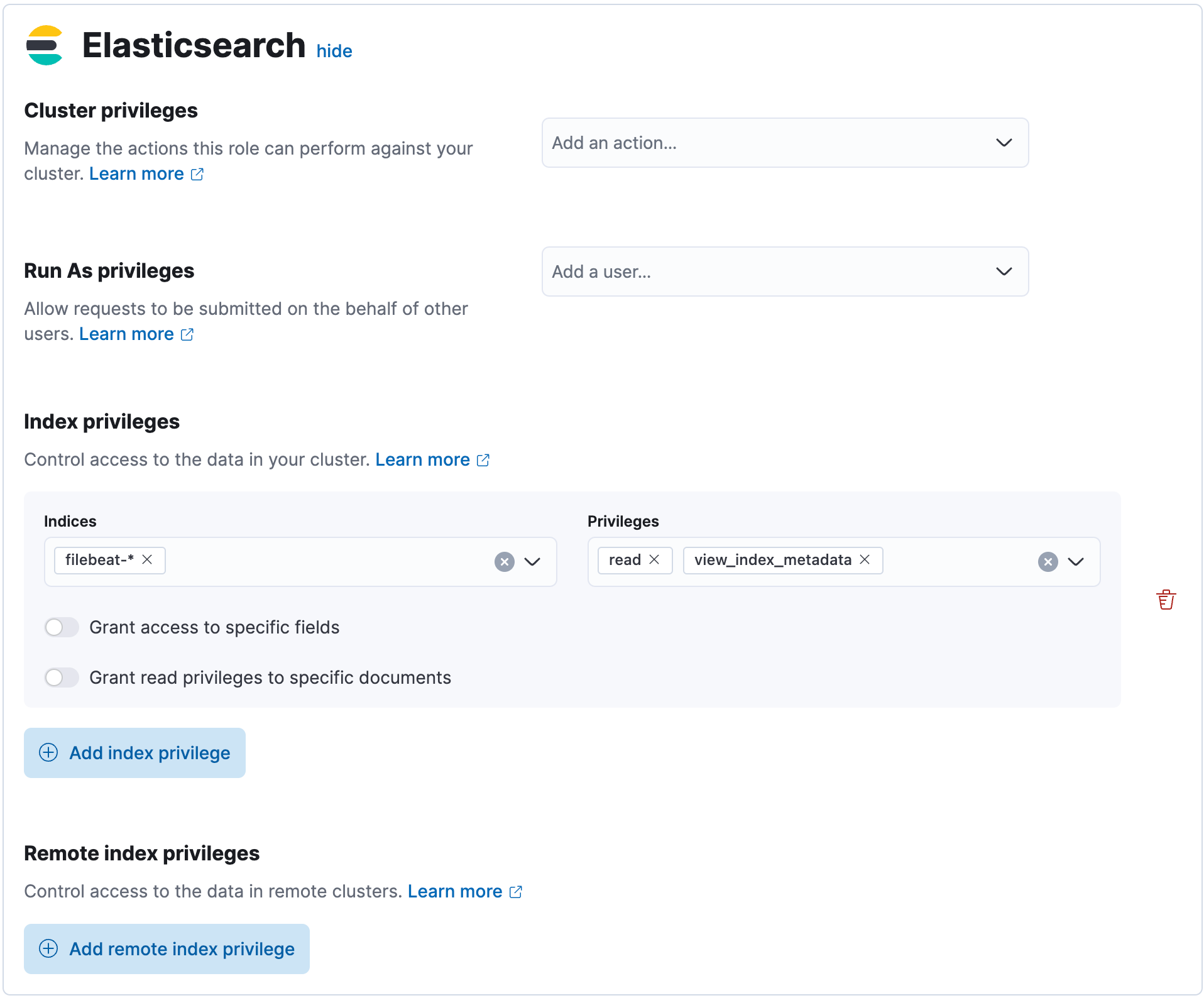
Kibana Role Management Kibana Guide 8 3 Elastic

App Consent Grant Investigation Microsoft Docs
Securelink Enterprise Access Third Party Remote Access
What Is Privileged Access Management Pam Explained Security Wiki

How To Detect And Prevent Industrial Espionage With Examples Ekran System